5 Copyright © Acronis International GmbH, 2002-2013.
13.3 Editing a task ............................................................................................................................82
13.4 Deleting a task .........................................................................................................................82
13.5 Viewing task logs .....................................................................................................................82
13.6 Viewing task details .................................................................................................................82
14 Managing Recovery Points ................................................................................................... 85
14.1 Adding a backup location ........................................................................................................86
14.2 Virtual Machines catalog .........................................................................................................87
14.3 Recovery Points list ..................................................................................................................87
14.4 Summary tab ............................................................................................................................88
14.5 Operations on selected items ..................................................................................................88
14.5.1 Restore ........................................................................................................................................................... 88
14.5.2 Exchange Recovery ....................................................................................................................................... 89
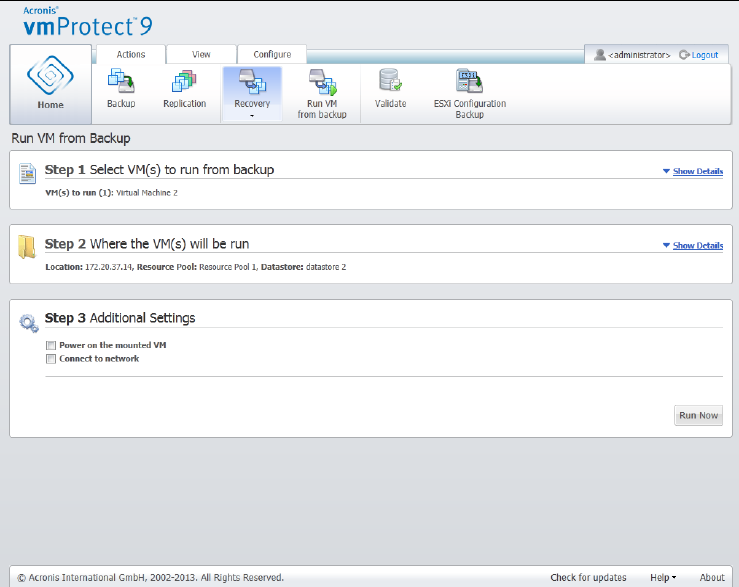
14.5.3 Run VM from backup .................................................................................................................................... 89
14.5.4 File recovery................................................................................................................................................... 89
14.5.5 Validate .......................................................................................................................................................... 89
14.5.6 Delete ............................................................................................................................................................. 89
15 Other Operations ................................................................................................................. 90
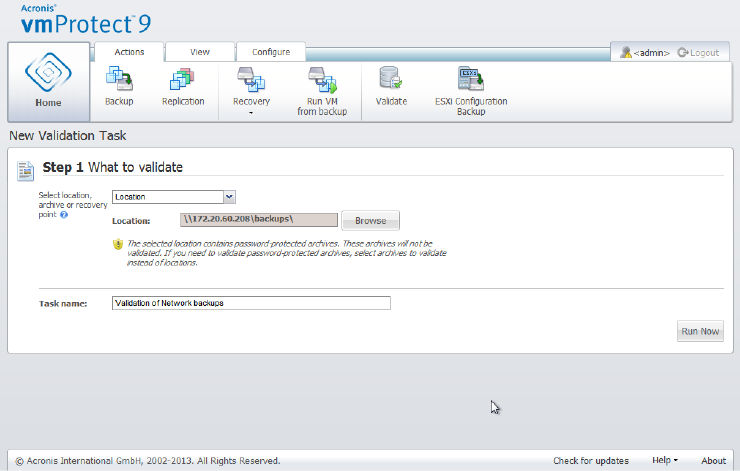
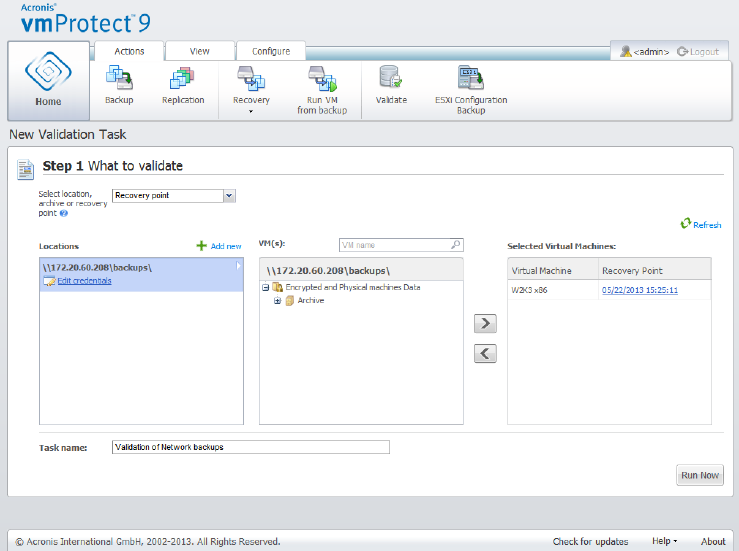
15.1 Validating backups ...................................................................................................................90
15.1.1 What to validate ............................................................................................................................................ 90
15.2 Managing mounted VMs .........................................................................................................92
15.2.1 Mounted VMs list .......................................................................................................................................... 92
15.2.2 Mounted VMs details ................................................................................................................................... 92
15.2.3 Unmounting VMs .......................................................................................................................................... 93
15.3 Managing logs ..........................................................................................................................93
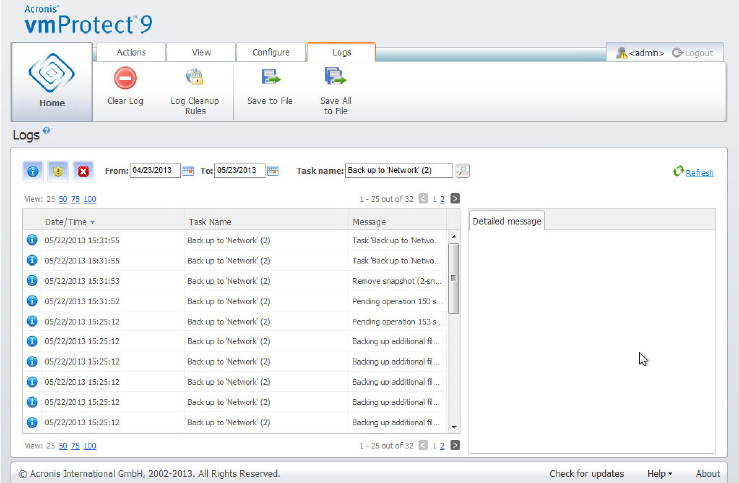
15.3.1 Logs list ........................................................................................................................................................... 93
15.3.2 Clear logs ........................................................................................................................................................ 94
15.3.3 Log cleanup rules ........................................................................................................................................... 95
15.3.4 Save logs to file .............................................................................................................................................. 96
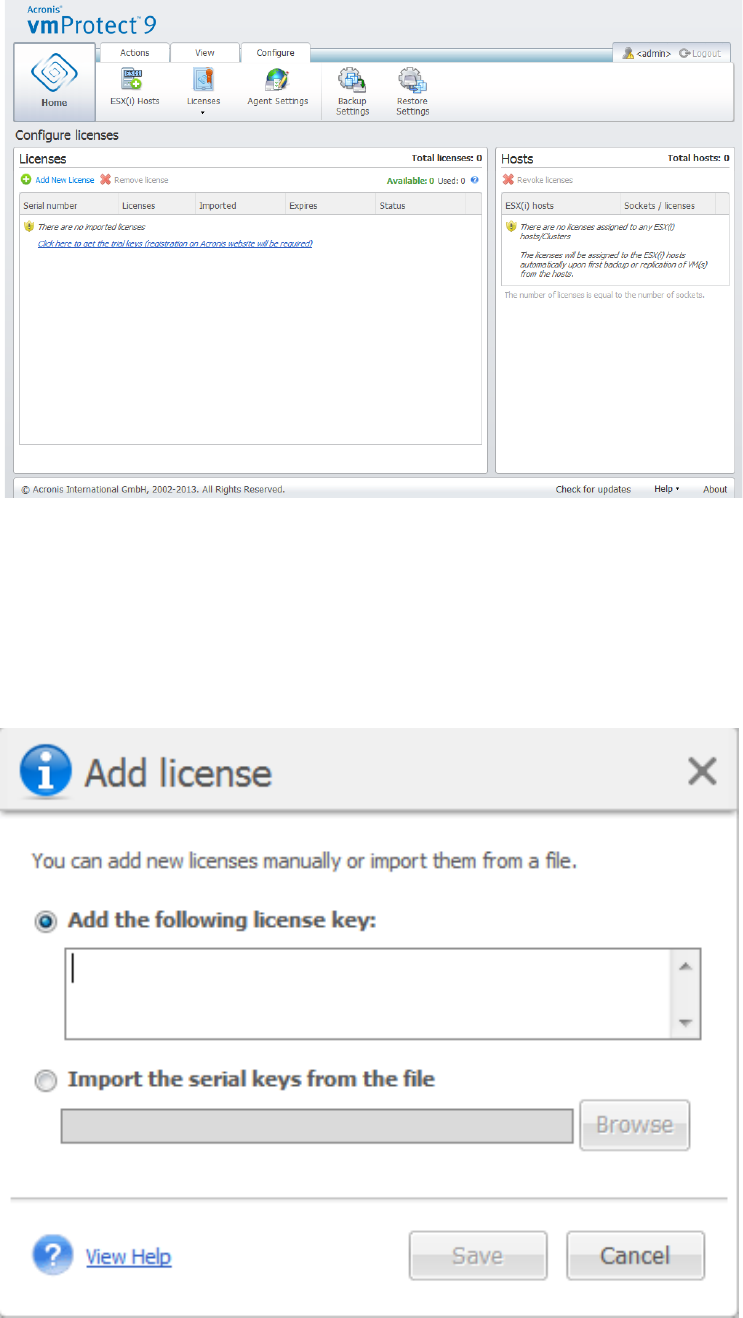
15.4 Managing licenses....................................................................................................................96
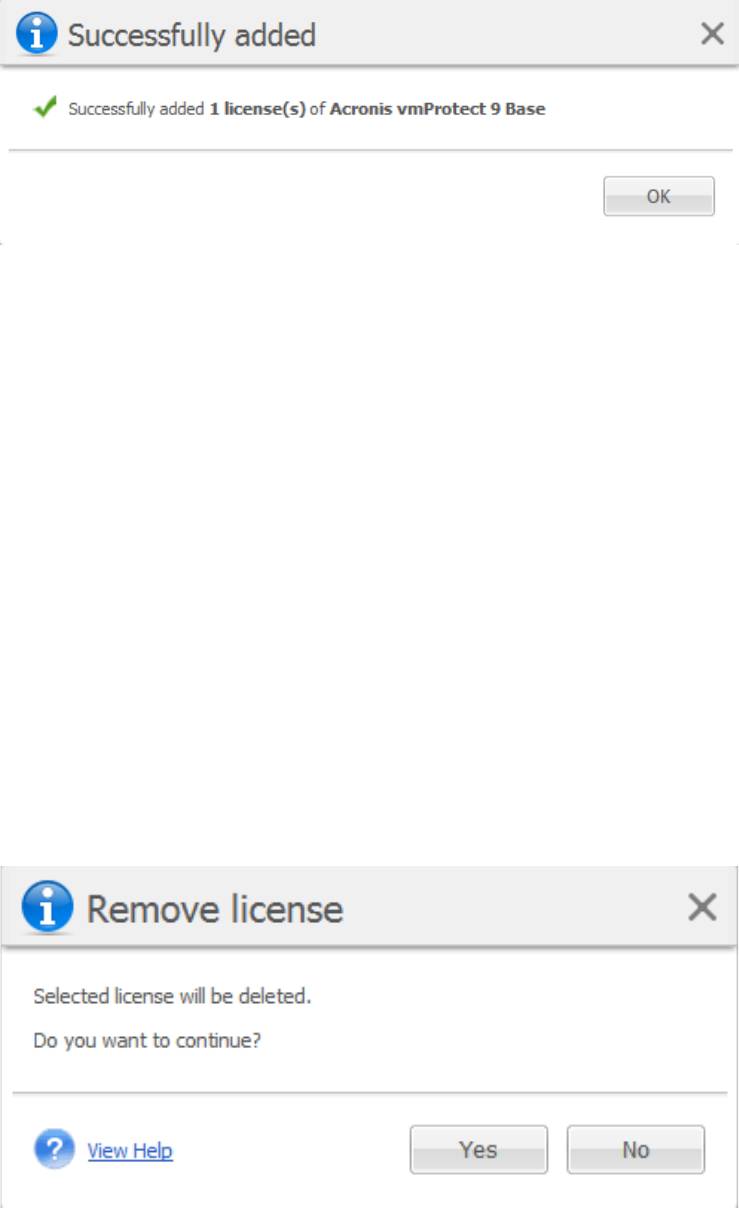
15.4.1 Adding license ................................................................................................................................................ 97
15.4.2 Adding license failure .................................................................................................................................... 98
15.4.3 Removing license/ESX(i) host ....................................................................................................................... 98
15.4.4 Available Licenses .......................................................................................................................................... 99
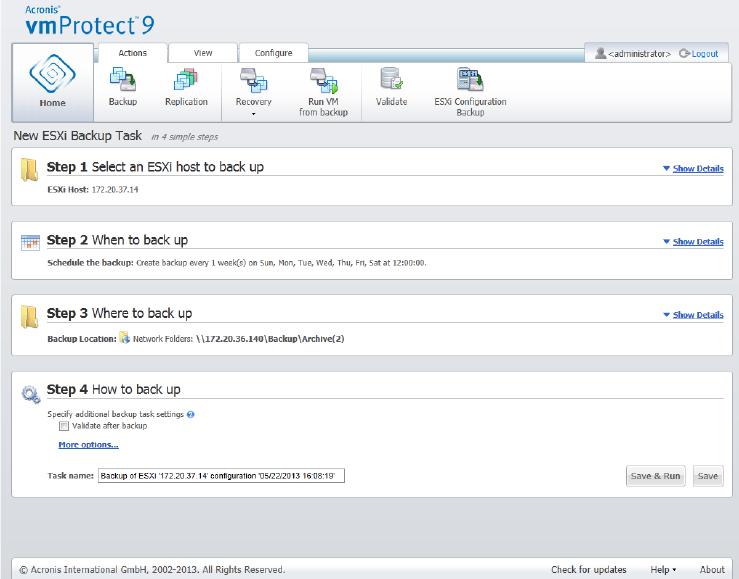
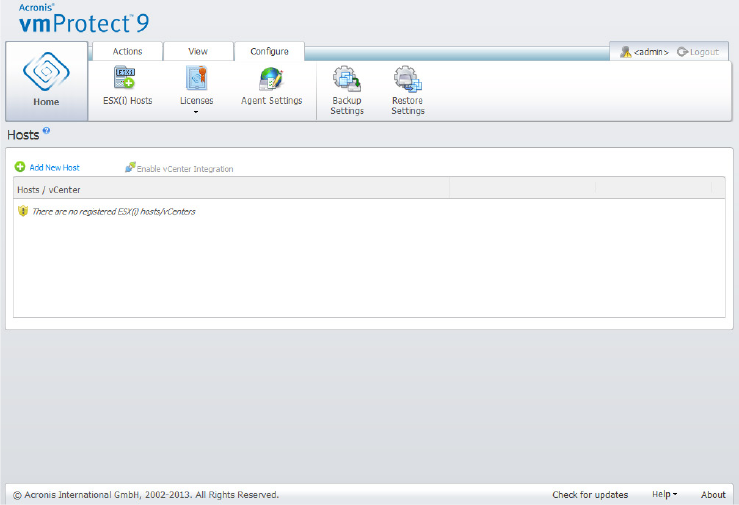
15.5 Managing ESX(i) hosts..............................................................................................................99
15.5.1 ESX(i) hosts list ............................................................................................................................................... 99
15.5.2 Adding ESX(i) host ....................................................................................................................................... 100
15.5.3 Adding an ESX(i) host which is a part of vCenter ...................................................................................... 101
15.5.4 Login credentials ......................................................................................................................................... 101
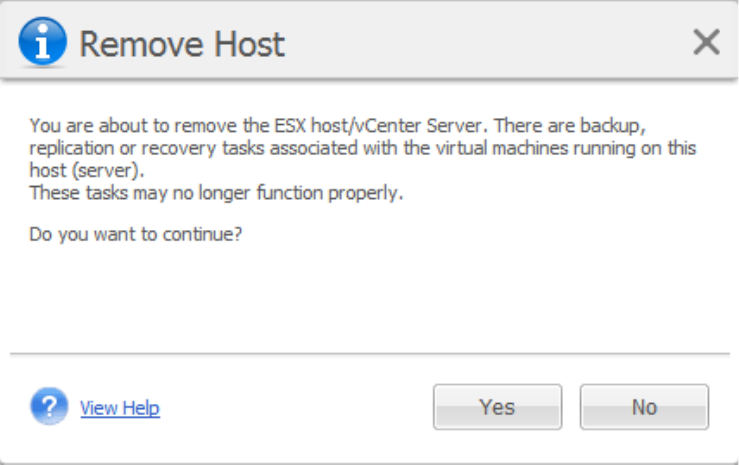
15.5.5 Removing ESX(i) host .................................................................................................................................. 102
15.6 Managing settings ..................................................................................................................103
15.6.1 Cloud Backup Subscription ......................................................................................................................... 103
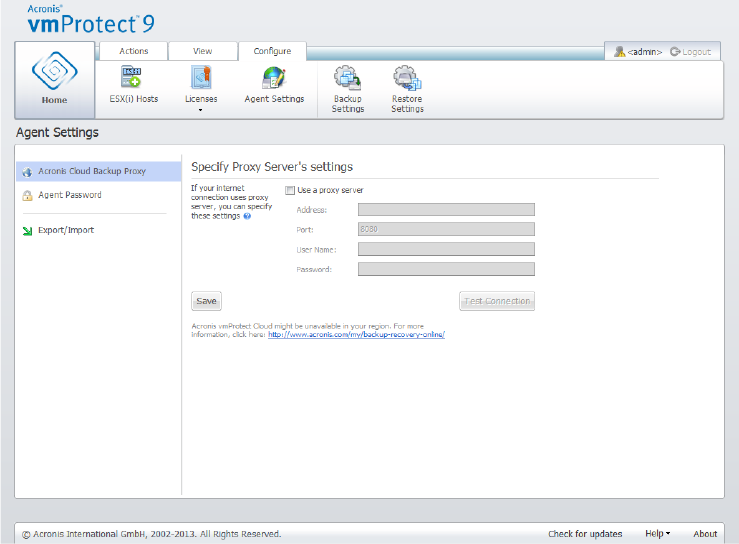
15.6.2 Cloud Backup Proxy..................................................................................................................................... 103
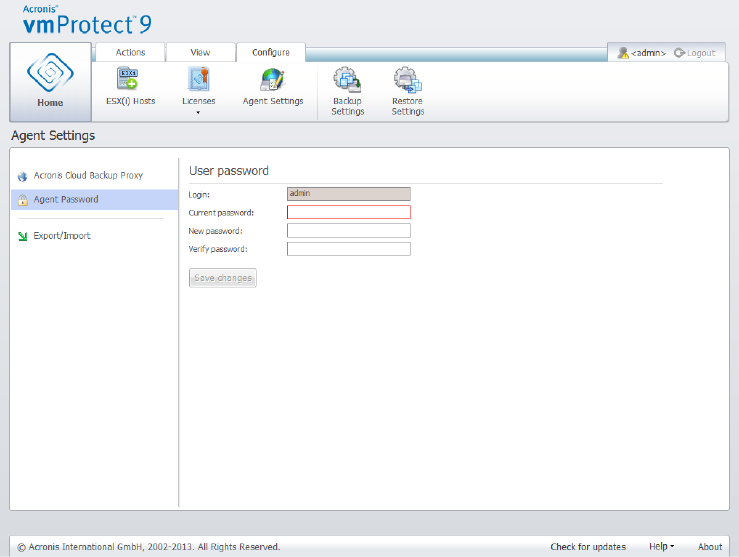
15.6.3 Agent Password ........................................................................................................................................... 105
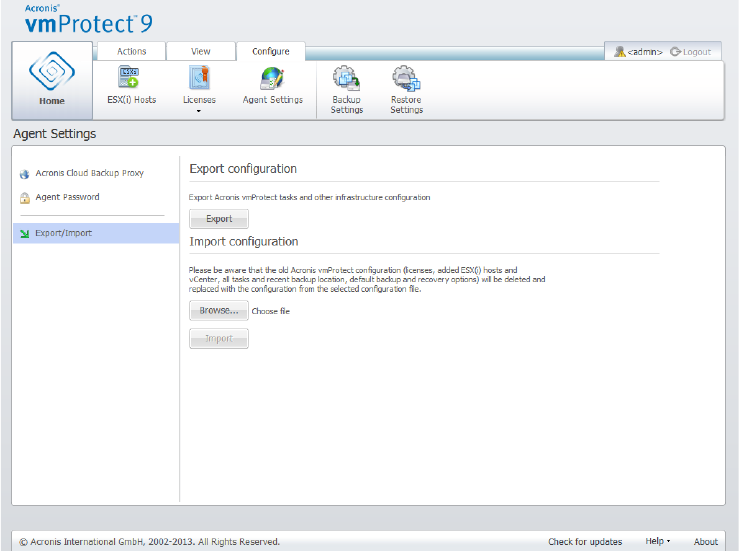
15.6.4 Export/Import Configuration ...................................................................................................................... 105
16 Best Practices .................................................................................................................... 108
16.1 Backing up virtual machines to a network share ...................................................................108